Stop scrambling for audits. Continuous compliance monitoring provides real-time visibility into your security posture. Here's how it works.
For all those businesses drowning in compliance tasks, an effective continuous monitoring program promises relief. But here's the brutal truth: Most people trying to "automate compliance" just swap one set of manual tasks for another. You're no longer hunting screenshots, but you're still buried in alerts from your compliance monitoring system, remediation tickets, and audit coordination.
So, let’s break down why traditional periodic compliance fails, what most "continuous compliance" platforms get wrong, and how to implement an approach that actually works. We'll show you we’ve built Mycroft to combine automation, intelligence, and operational support to keep you secure and audit-ready without grinding your product roadmap to a halt.
It's Q4. Your auditor just sent the evidence request list. Your engineering team (already underwater with the product roadmap) is now being pulled into Slack channels with messages like "URGENT: SOC 2 Evidence Needed." Sound familiar?
This is how most of the businesses I talk to approach their compliance processes: Ignore it for 11 months, then scramble when the audit deadline looms.
And it plays out in predictable patterns:
In the end, everybody breathes a collective sigh of relief when you pass the audit, but it’s a brief moment of reprieve when you remain vulnerable 364 days a year.
This approach to compliance (treating it as a periodic hurdle to overcome and then forgetting about it until the next hurdle comes round) is fundamentally flawed. Not just because of the obvious cycle of panic it unnecessarily creates, but because it creates real dangers:
There's a much better way to keep up with compliance standards all the time: Continuous compliance monitoring.
Continuous compliance monitoring means you always have real-time oversight of your security posture, with the system automatically checking that controls are functioning as designed and alerting you the moment something starts to drift out of line. Unlike periodic audits which give you snapshots of compliance at a certain point in time, continuous monitoring gives you a constant view of your security environment.
This ongoing visibility is built on four foundational capabilities:
Why continuous compliance matters:
Most organizations know they need continuous compliance. The question is: How do you actually achieve it? The conventional wisdom says, "Buy a GRC platform and automate everything." But that advice can be misleading.
Most guidance follows a pretty well-worn pattern:
Why this sounds great on paper:
On paper, this sounds like the perfect solution. Unfortunately, the reality is more complicated.
Here's what actually happens when you implement a typical continuous compliance platform:
Automated checks will throw up red flags, but then you've got to figure out what they actually mean; someone still needs to contextualize them.
Your cloud scanner flags an open port. Is it a vulnerability or required for a specific integration? The tool can't tell you. You've traded manual evidence collection for manual triage and investigation.
Traditional continuous compliance platforms handle compliance reporting, but not compliance operations.
You still need:
You thought you were simplifying your security ops, but what you really did was just add another layer to a system that's already way too complicated. Each new tool comes with its own learning curve, integration headaches, and operational overhead. Not quite the simplification you were hoping for.
Related: A deep dive into how to eliminate security tool sprawl
The dirty secret of "automated compliance": You still need someone on your team to:
That's where most organizations run into trouble. They invested in automation, but their security and compliance teams are still too busy to get anything done. Just different tasks this time round.
Even if you pass all the automated tests, it doesn't mean your controls are actually any good:
Continuous compliance isn't just about having the right tools - it's about having the right way of working. This is what actually works:
True continuous compliance requires three layers:
Most organizations focus on #1, dabble in #2, and sell out on #3.
Here’s what effective compliance really looks like:
Instead of juggling multiple dashboards:
Think of it as a Risk Operations Center (ROC)—a centralized hub that doesn't just report on compliance, but actively manages it.
Context-aware systems go beyond simple rule checking to understand what matters in your specific environment:
Example: A traditional platform flags 50 medium-severity vulnerabilities across your cloud infrastructure. A context-aware system tells you which 5 actually expose customer data and require immediate remediation, and routes them to the right engineer automatically.
Third-party risk doesn't pause between annual questionnaires. Effective continuous compliance extends monitoring to your entire vendor ecosystem:
Identifying issues is only half the battle; you need systems that drive them to resolution:
In the end, mature continuous compliance programs do a lot more than just collect evidence; they actively manage the whole audit lifecycle:
This is the model Mycroft was built around: A Risk Operations Center that combines platform automation with forward-deployed GRC engineers. You get the tools and the operational support—so your team can focus on building your product, not chasing compliance screenshots.
When you implement continuous compliance properly, the benefits extend far beyond "always audit-ready." Done right, continuous compliance becomes a strategic business enabler that impacts your bottom line, operational efficiency, and growth trajectory.
The traditional "always-on" compliance stack can really add up. Here are some ballpark figures a startup-scale traditional stack (not full enterprise MSSP) can expect to pay annually:
And then there's the deeper financial impact that goes beyond just chopping vendors. Think about it: what about the hidden costs of the traditional way of doing things? For example, how about the hours your engineers spend on product development instead of stuck on compliance? Then there's the issue of delayed enterprise deals because you "only" have time to "work on compliance"...And all the features that never see the light of day because your team's too busy prepping for audits.
Okay, so the financials look great, but the time savings might just be even more valuable. Think about how long it usually takes to get SOC 2 Type II compliant:
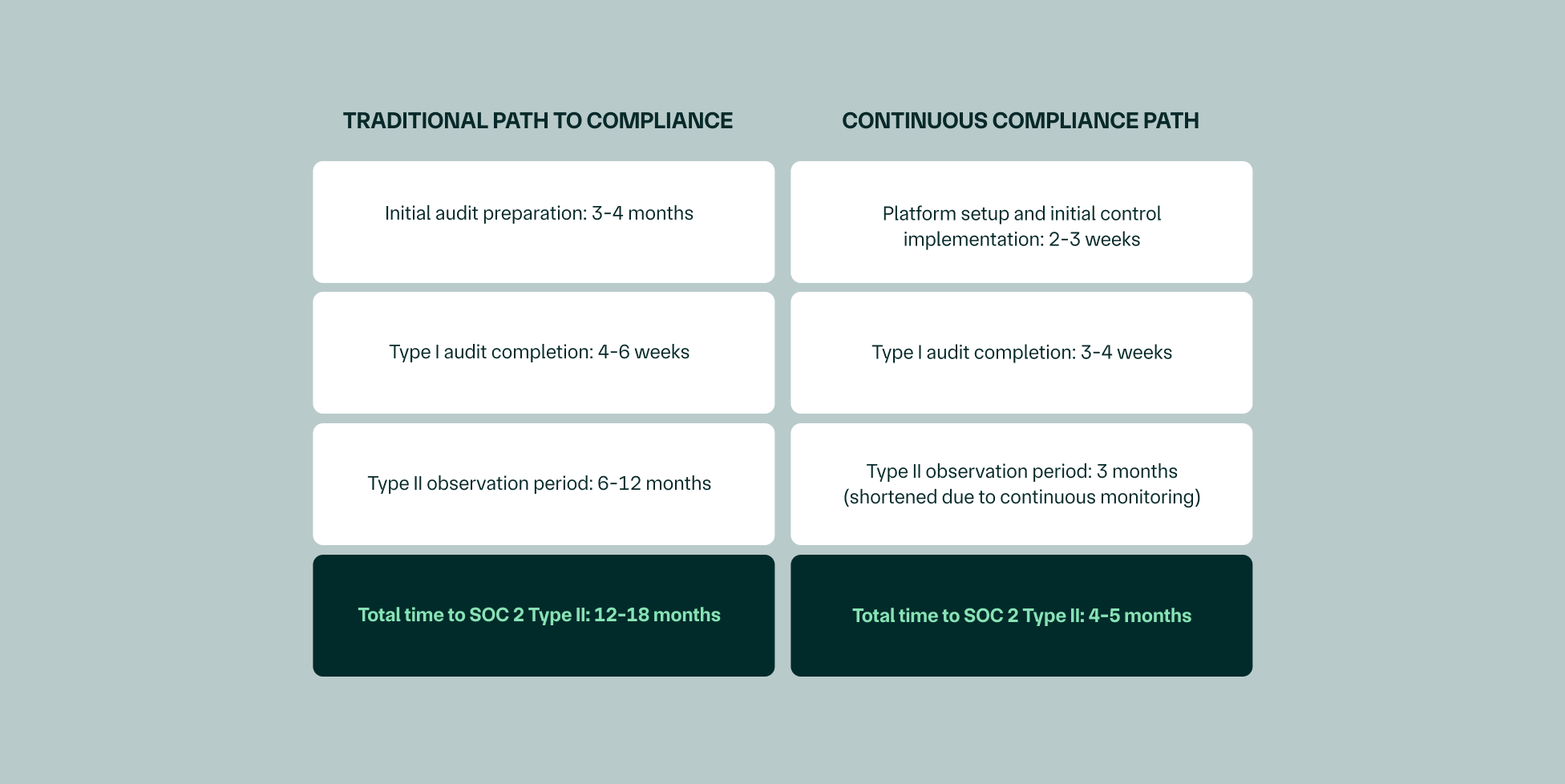
Traditional path to compliance:
Total time to SOC 2 Type II: 12-18 months
Continuous compliance path:
Total time to SOC 2 Type II: 4-5 months
Time saved: 8-13 months of your team's attention that can stay focused on product development instead of audit preparation.
But even after you've got that initial certification in the bag, the time savings keep on coming. The annual recertification audits that normally take up 4-6 weeks of planning and coordination become pretty much a breeze. Your auditor just logs into your platform, pulls the evidence they need, and that's it.
Beyond direct cost and time savings, continuous compliance creates strategic advantages that are harder to quantify but equally important:
So how do you actually make this work? Here's the basic plan:
Before you start implementing continuous compliance, take some time to figure out what you've got to work with:
Key questions to ask yourself:
With your current state documented, the next step is establishing clear requirements for your continuous compliance program:
At this point, you've got a choice to make:
Mycroft takes the second approach—we provide the platform and the Risk Operations Center that runs it for you.
Rather than attempting a big-bang transformation, successful implementations follow a phased approach:
Continuous compliance isn't a "set it and forget it" proposition. To really make it work, you need to be willing to keep tweaking and refining:
❌ Don't get caught up in silly promises to get compliant in a week (compliance actually takes time)
❌ Be wary of products that promise automation but actually just drop a bunch of config and tuning work on you (you want to simplify your life, not get a new job)
❌ If the integration support is weak, watch out for gaps in visibility
❌ Audit-focused only tools are basically useless - you want security, not just compliance theater
As you can see, Mycroft was designed to check every box on this list—and to provide the operational support that makes continuous compliance sustainable.
Continuous compliance isn't just a nice-to-have - it's a must. Regulations are piling up, your infrastructure is getting more complicated by the day, and the cost of not being compliant is just going up and up.
But just getting a tool isn't enough - you need a whole operating model that combines automation, intelligence, and actual operational support.
The real question isn't so much "should I do this" but "how am I going to get it done?"
Ready to see what continuous compliance looks like with Mycroft?
Book a demo to learn how our AI-powered Risk Operations Center can consolidate your security stack, automate compliance operations, and free your team to focus on growth—not audits.
Continuous compliance monitoring is the automated, real-time process of ensuring your organization's security controls, policies, and systems remain aligned with regulatory obligations and industry frameworks, without relying on periodic audits to identify gaps.
Traditional compliance relies on point-in-time audits (annual or semi-annual), which means compliance drift can go undetected for months. Continuous compliance provides real-time visibility, automated monitoring, and immediate alerting when violations occur.
The key benefits when organizations achieve continuous compliance include:
At minimum, you need:
However, managing these as separate point solutions creates operational complexity and gaps in visibility. That's why many organizations consolidate into a unified platform like Mycroft, which integrates all five capabilities into a single Risk Operations Center. This approach eliminates tool sprawl, provides centralized visibility across your entire security posture, and includes the operational support to actually run your compliance program—not just monitor it.
Automation handles repetitive tasks like evidence collection and control monitoring, but human oversight is still required for:
The best solutions combine automation with operational support.
Implementation timelines vary:
Organizations with existing compliance programs can often achieve continuous monitoring faster than those starting from scratch.
Continuous compliance can support maintaining continuous compliance for any framework with defined controls, including:
By continuously monitoring controls in real-time, continuous compliance monitoring tools:
With the right platform and operational support, organizations can typically achieve:
However, be wary of vendors promising "compliance in one week"—that's usually checkbox compliance, not real security. Quality auditors need time to properly assess your controls.
AI agents can:
The key is that AI should augment human analysts, not replace them entirely.