The organizations that thrive in 2026 and beyond won’t treat security as a bottleneck. They’ll treat security as a connected system.

Third-party risk management (TPRM) is the process of identifying, assessing, and mitigating security and compliance risks from vendors, suppliers, and service providers in your technology stack. Every third-party tool represents potential attack vectors, data exposure, and business continuity risks that could impact your entire organization.
But in practice, TPRM has become a cumbersome, disjointed, and often ineffective mess that slows business decisions without meaningfully improving posture. For enterprise CISOs managing hundreds or thousands of vendor relationships, legacy methods create more problems than they solve.
If you're operating enterprise TPRM today, it probably goes something like this:
A new vendor request comes in. Security sends a lengthy vendor questionnaire. You wait weeks for responses, which are often incomplete or generic. Then you manually review compliance documents like SOC 2 reports. After multiple back-and-forth discussions, the vendor is approved or rejected based on limited information.
This approach fails predictably because it's built on fundamentally flawed assumptions about how modern enterprises operate at scale.
Every vendor assessment starts from scratch, even when evaluating similar tools or renewing existing relationships. Enterprise security teams waste cycles recreating questionnaires and chasing the same compliance documentation repeatedly across hundreds of vendors.
Your GRC team uses one platform, security uses another, and procurement operates in its own system. When TPRM tools are disconnected from other critical enterprise systems, risk data gets trapped in siloes instead of informing the integrated business decisions.
You approve vendors based on their current security posture, but that posture is constantly changing without you realizing it. Breaches happen, certifications lapse, and risks shift, but you remain unaware until annual renewals.
You have little leverage with your most valuable vendors, so they provide only minimal security information. Your TPRM program becomes a "checkbox exercise" rather than meaningful enterprise risk management.
Enterprise security leaders often need clarity on the distinction between third-party risk management and vendor risk management, as these concepts address different scopes of business relationships and risk exposure.
Vendor risk management focuses specifically on commercial suppliers and service providers with contractual relationships. This includes software vendors, cloud service providers, consultants, and other businesses providing products or services in exchange for payment.
Third-party risk management encompasses all external entities that could impact enterprise security or compliance, including vendors, business partners, subsidiaries, joint venture partners, contractors, and even customers in certain contexts.
For enterprise CISOs, scope differences create strategic implications:
Comprehensive enterprise TPRM platforms address both vendor and broader third-party relationships through unified risk assessment and monitoring capabilities. This provides complete visibility into external risk exposure while maintaining appropriate oversight for different relationship types.
Strategic advantage comes from implementing comprehensive third-party risk management rather than limiting scope to traditional vendor relationships. Enterprises with broader TPRM coverage identify and mitigate risks that vendor-only programs miss, providing CISOs with complete external risk visibility.
Modern enterprises need TPRM solutions that handle the full spectrum of third-party relationships while providing scalable assessment and monitoring capabilities that support business velocity and regulatory compliance at global scale.
Enterprise CISOs need TPRM solutions that handle the scale and complexity of global business environments. Legacy "death-by-spreadsheet-driven" approaches simply can't keep up when managing vendor portfolios across global business units and regulatory environments.
Enterprise-grade TPRM software must be automated, embedded, continuous, and business-aligned:
Modern enterprise CISOs need TPRM platforms that transform third-party risk management from an operational burden into a strategic business enabler.
Effective enterprise TPRM requires systematic approaches that balance security rigor with business velocity at scale. Organizations that excel at enterprise third-party risk management follow proven practices designed for complex, global operations.
Risk-based vendor prioritization: Categorize vendors by business impact and data access to allocate CISO resources efficiently. Streamline low-risk vendors while enhancing scrutiny for mission-critical providers.
Standardized assessment frameworks: Establish consistent vendor evaluation criteria and workflows across the organization to ensure fair, predictable treatment at scale.
Continuous monitoring: Extend risk management beyond initial approval to provide real-time visibility into your vendor ecosystem without manual oversight.
Collaborative workflows: Engage cross-functional teams in vendor evaluation through defined processes. Shared responsibility ensures comprehensive risk assessment while aligning with business needs.
Automated documentation: Maintain comprehensive, audit-ready records of vendor assessments, approvals, and monitoring without manual effort to support compliance and risk decision-making.
Performance measurement: Evaluate TPRM effectiveness through metrics like assessment times, vendor incidents, and compliance violations. Continuously improve the program to align with evolving business needs.
Comprehensive TPRM platforms that automate assessment workflows, provide continuous monitoring, and integrate across your enterprise systems can transform third-party risk management from an operational burden into a strategic business enabler.
Mycroft's AI-powered TPRM solution delivers these enterprise-grade capabilities in a single, integrated platform. By automating vendor assessments with the utilization of AI Agents, identifyingmonitoring risks in real-time with continuous open-source intelligence monitoring, and seamlessly integrating with your existing GRC processes through an API-first approach, Mycroft empowers you to take control of third-party risk and unlock new business opportunities.
Learn more about Mycroft's TPRM solution or book a demo with a member of our team.
Vendor management covers commercial suppliers with contracts (software vendors, cloud providers, consultants). TPRM encompasses all external entities affecting security or compliance, including business partners, subsidiaries, contractors, and customers. Enterprise CISOs need comprehensive TPRM because vendor-only programs miss critical non-commercial third-party risks.
Enterprise TPRM platforms range from $50,000-$500,000+ annually, depending on vendor count and integrations. Comprehensive automated platforms, like Mycroft, often provide better ROI than multiple point solutions by eliminating manual processes and scaling with business growth without proportional staff increases.
Automated TPRM delivers a substantial reduction in assessment cycle times, eliminates manual documentation effort, prevents vendor security incidents, and accelerates deal closure. Strategic benefits include improved vendor relationships, better regulatory compliance, and the ability to scale vendor portfolios without proportional staff increases.
Implementation ranges from 30-90 days for organizations with established GRC processes to 6-12 months for companies requiring significant policy development. Start with core assessment workflows and expand capabilities incrementally for faster deployment.
Essential integrations include ERP systems (vendor discovery), procurement platforms (workflow automation), SIEM tools (security monitoring), identity management (access controls), and GRC platforms (compliance reporting). API connectivity with vendor systems enables automated evidence collection and eliminates manual data transfer.
Mycroft integrates with over 150+ integrations to automate everything you need in a single place.
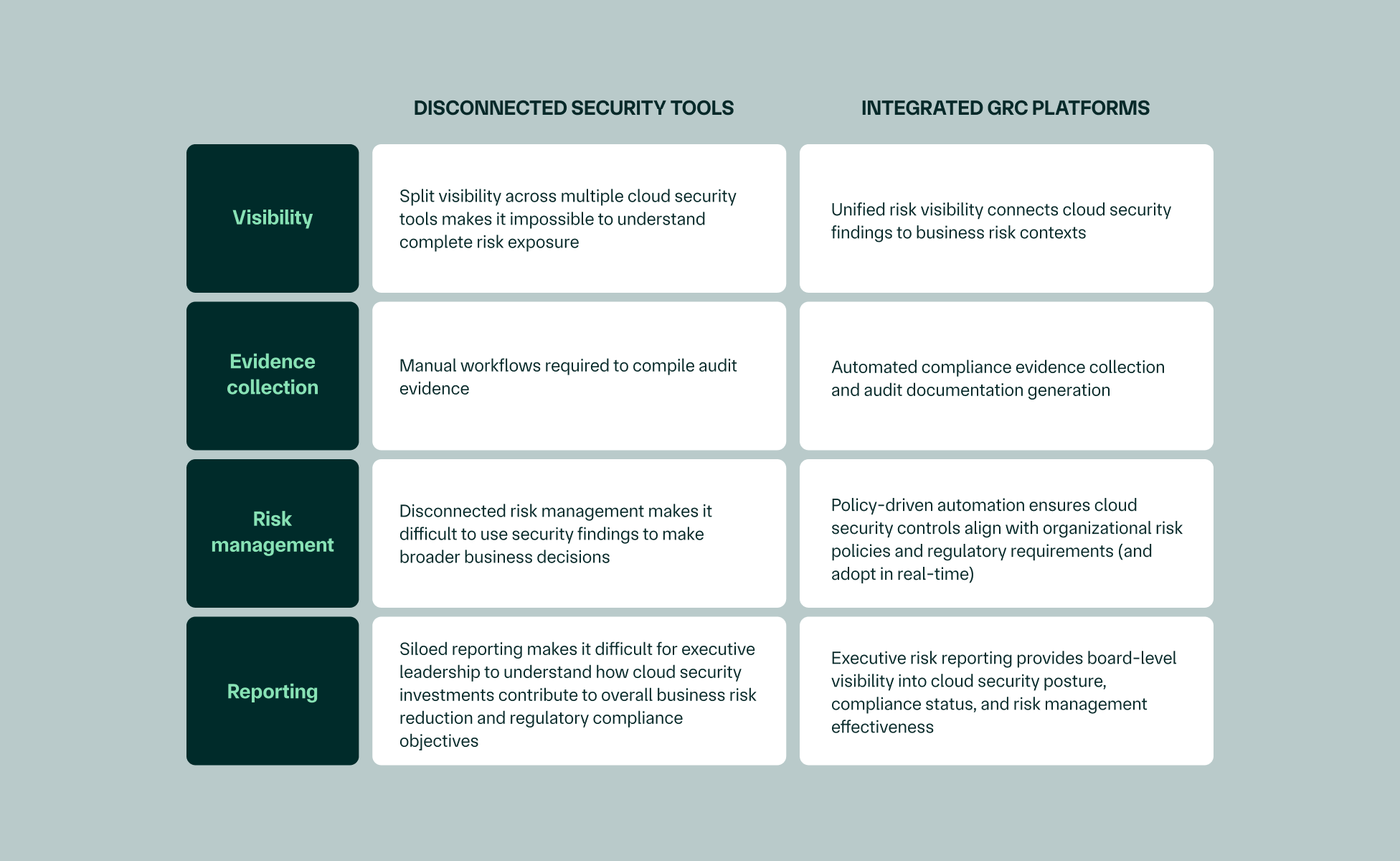
Most companies are drowning in security tools that don't talk to each other. Mycroft takes a different approach: one platform that integrates cloud security with risk management, built for organizations innovating with AI.
With Mycroft you’ll get:
CTA block
The AI evolution is already here. Is your cloud security strategy keeping up?
Schedule a Demo and see how Mycroft helps you stay secure, compliant, and investor-ready, without slowing down innovation and growth.
CI/CD Pipelines: Continuous Integration/Continuous Deployment automated workflows that build, test, and deploy code changes. Modern development teams use CI/CD to ship software updates rapidly.
CNAPP: Cloud-Native Application Protection Platform that provides security across the entire application lifecycle, from development through production runtime.
Configuration Drift: When cloud infrastructure settings change over time, moving away from approved security configurations. This happens naturally as teams make updates without centralized oversight.
Containers: Lightweight, portable software packages that include everything needed to run an application. Popular containerization platforms include Docker and Kubernetes.
CSPM: Cloud Security Posture Management tools that continuously monitor cloud configurations against security best practices and compliance requirements.
GPU cluster configuration: Interconnected computing systems, containing multiple Graphics Processing Units (GPUs), each of which works together on large tasks like AI and scientific simulations.
Hypervisor: Software that creates and manages virtual machines on physical servers. Cloud providers use hypervisors to isolate customer workloads from each other.
IaC (Infrastructure as Code): Managing cloud infrastructure through code files rather than manual configuration. IaC allows teams to version control and automate infrastructure deployment.
Microservices: Application architecture that breaks large applications into smaller, independent services. Each microservice can be developed, deployed, and scaled separately.
Multi-cloud: Using multiple cloud providers (AWS, GCP, Azure) for different services or redundancy. Multi-cloud strategies provide flexibility but increase security complexity
Perimeter-based Security: Traditional security model that focuses on protecting network boundaries. This approach becomes less effective in cloud environments where there are no clear perimeters.
Serverless Functions: Code that runs on demand without managing servers. Examples include AWS Lambda and Azure Functions, which execute code in response to events.
Shared Responsibility Model: Security framework where cloud providers secure the infrastructure while customers secure their data, applications, and access controls.